
Cloud Antivirus
WHAT IS WRONG WITH TRADITIONAL ANTIVIRUS?
Traditional antivirus products are based on signature recognition performed on endpoints. That is a failing strategy because:
the number of recognized threats has grown so huge that it is impractical to keep endpoint systems updated with signatures, and it’s impossible for endpoints to compare files against all known signatures
hackers and cybercriminals are using botnets and other techniques to propagate zero-day threats before signatures can be distributed to endpoints
Often no signatures at all exist for targeted threats aimed at single individuals or organizations. Hackers are using techniques like malware crypters, server-side polymorphism and QA testing so they cannot be recognized by signatures.
For these reasons, it is no wonder most information security experts question the ability of signature-based antivirus products to block the newest and most dangerous forms of malware.
CLIENT | CLOUD ARCHITECTURE
The “fat client” architecture of traditional antivirus products relies on heavyweight modules on endpoint systems to compare suspicious files with threat signatures. A client/cloud architecture fundamentally changes this dynamic. Only a very small client is needed on the endpoint. This client finds new files and creates hashes (signatures) of those files. The hashes are sent to a cloud-based server and compared with a large signature database. Responses are sent back to the endpoint system.
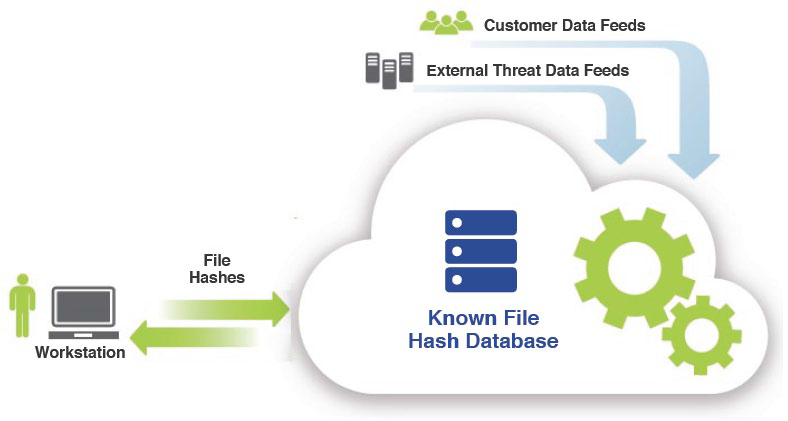
The client / cloud architecture has tremendous benefits over traditional antivirus products:
- very little processing takes place on the endpoint, so there is no impact on end-user productivity
- there is no appreciable impact on bandwidth usage or network performance, since only a few dozen hashes per system are exchanged over the network (typically about 120KB per day) instead of thousands of new threat signatures
- the cloud-based system can host huge signature databases and use massive servers to perform pattern matching, so signature comparisons are more complete and faster
- the cloud-based system gets real-time threat data feeds from test laboratories, antivirus clearinghouses, security vendors, thousands of enterprises and millions of users, so zero-day threats can be blocked as soon as they are identified
- roaming and remote users can be protected from zero-day attacks as soon as they connect to the Internet
- systems administrators don’t need to spend time installing fat clients or distributing signature updates to every endpoint system
Fat-client antivirus products are effectively obsolete. A client/cloud architecture is the only way to make real-time signature-matching practical and effective.
Test it for free
Fill out the form and submit and we will contact you
 Very high protection efficiency
Very high protection efficiency
 Remote installation and configuration
Remote installation and configuration
 Management from any location
Management from any location

















